December 18, 2022
August 28, 2018
Today I ask: Why is the USTA Men’s Singles Cup larger than the Women’s Singles Cup?
It is clear to me that women face unique problems in the workplace that their male counterparts do not have. One of these problems is known as the gender wage gap. Most estimates show women only earning about 85% of the salary of their male counterparts. Different studies come to different conclusions as to why this is occurring.

2018 USTA US Open Champion Cups
Today I went to the USTA US Open’s opening day. Looking through the program, I recognized that both winners receive the same prize money of $3.8 million. This should not be shocking given it is 2018, however, in other parts of the economy/society this is certainly not true.
That said, later in the day, something caught my eye that bothered me.
While at the championship, I took a picture standing next to the USTA US Open Singles Champion cups. I say “cups” plural because there is a large sterling silver cup for the Men’s Singles Champion and a second identical sterling silver cup for the Women’s Singles Champion. Indeed, the cups are beautiful and valuable.
There is only one problem: as you can see in the photo the cups are not actually identical.
The men’s trophy is about 1/3 larger… than the women’s trophy.
The difference in the size of the cups bothered me enough to write this blog. I did take a short 10 minute online look but was unable to find reliable information or specifications regarding the history or design of the cups.
I ask the both the USTA and the CUNY Commons community….. is there an inherent or symbolic inequality in having the Men’s Singles Cup larger than the Women’s Singles Cup?
Thoughts?
Please comment below and thank you for reading.
March 13, 2018
Thank You – Dr Hawking
It’s not often a Braking News Alert brings me to tears. But at 11:50 last night, a BBC Alert announcing the death of Dr. Stephen Hawking did just that. Dr. Hawking has been a central figure in my life. Someone I admire greatly. I consider him one of mankind’s greatest.
I read just about every piece of his work I could get my hands on over the years. He had an amazing way of describing the most complex scientific theories in ways that anyone could understand. His books and works have been the basis of countless intellectual conversations I have engaged in over the years. I watched him play himself on Star Trek growing up… and the Big Bang Theory in more recent years. I found his sense of humor and personality… mesmerizing.
He taught me more about the universe and our existence than any other person, religion or institution. I wrote him a fan letter in 2007 or 2008 and one of his grad students responded. I am glad I took the time to thank him for his work.
He was one of the most important minds of my lifetime.
Thank you Dr. Hawking for everything.
I will miss you.
March 7, 2018
I had class tonight…. did you?
Tuesday afternoon: media declares major NYC area snowstorm for Wednesday
Tuesday 9:17pm: I post a message to my courses Slack channel advising students that Wednesday’s 6PM class will be moved online to a zoom.us conference room. I make it clear that the course will meet even if the college closes.
Tuesday 10:13pm: 100% of students in the course confirm receipt of the message within Slack using Slacks “Simple Poll” app. That’s 100% of students confirming the message in under an hour. This was made possible due to Slacks push notification system and my amazing students.
Wednesday 10am: No snow. I go to work.
Wednesday 1pm: Snow
Wednesday 2:26pm: The college closes – canceling all remaining classes.
Wednesday 6:00PM: My PAD 713 class meets in a zoom.us online virtual room. I have 100% student attendance with everyone arriving in the room by 6:05pm. This was the first time I used the technology with these students.
What made this possible?
1) Planning
2) Funding for a zoom license (thanks student technology fee)
3) Amazing and dedicated students
January 30, 2015
If a corporation is a person – Why can’t it vote?
| If a corporation is a person – Why can’t it vote? Simple: it’s an immature underage person. #adamsantics |
October 2, 2014
3D Guns Have Now Arrived: Do we need new legislation?
I have spent the past few years researching the emerging field of 3D Printing. I presented on the topic at a NYS legislative committee roundtable. I warned at the annual meetings of both Academy of Criminal Justice Science and the American Society of Criminology that within the next 1-3 years, a viable metallic printing solution will become available. I predicted that once it does, chaos will follow. The ability to print full metallic small weapons and parts of larger weapons from home is a very dangerous ability for anyone to have. These weapons would not have serial numbers and would be untraceable.
I have been warning about it for 3 years… and now that has finally arrived.
Dubbed the “Ghost Gunner” this $1,200 device takes solid aluminum blocks and using a technology called computer-numerically-controlled milling, gradually grinds away at a solid block of aluminum until only the design is left. The process is completely computer controlled. The user just inputs the design (weapons schematics are available online) inserts a block of Aluminum and “hits” go. Many hours later a gun part made of solid aluminum emerges.
This technology has been used for years in iPhone and other electronics manufacturing. However, for the first time, the technology is being made affordable enough for home use.
(Wired Ran a Story on This Yesterday)
Here is where you can buy your very own “Ghost Gunner.”
Computer-numerically-controlled mills can make very dangerous objects. Now that they are being sold for home use manufacturing weapons without serial numbers has become easy. It is my belief that this type of technology is dangerous and should be regulated at both the Federal and State level.
One option could be to require federal registration for sale or ownership. Another policy option could require licensure for these devices.
I believe Congress and the States should pass legislation categorizing this device and institute legislation to keep these devices from being misused on a large scale.
There is not much time before thousands of these printers will be shipped around America.
I believe one was used to print this 80% Lower AR Receiver. Note: “315 In Stock.”
A possible scenario to leave you with: a criminal prints out a functioning small firearm and uses it to kill someone. The criminal can just put the firearm back in the machine that created it. The machine could then turn the murder weapon to dust.
Adam Scott Wandt, J.D., M.P.A., is an Assistant Professor of Public Policy at John Jay College of Criminal Justice, where he serves on both the Graduate faculty of the Digital Forensics and Cyber Security program and the Masters of Public Administration in Inspection and Oversight program. Professor Wandt is an Attorney and Counselor-at-Law in the State of New York.
Media requests on this issue should be sent to the attention of [email protected] with “Ghost Gunner” clearly identified in the subject line.
Professor Wandt On Twitter: @Prof_Wandt
September 21, 2014
iPhone 6 and iPhone 6 Plus
Being that my last blog was of such a serious nature… I am delighted to be blogging on something much more uplifting: The release of the iPhone 6 and iPhone 6 Plus.
I have made several different videos of varying depths: unboxing, examining, discussing, and comparing these phones.
Full 45 Minute (Six and Six Plus): Unboxing, Setup and Fist Impressions
[youtube]https://www.youtube.com/watch?v=4PDwHPQfTXI[/youtube]
Short 5 Minute (Six and Six Plus): Unboxing Only
[youtube]http://www.youtube.com/watch?v=FkDtQSe045s[/youtube]
[youtube]https://www.youtube.com/watch?v=bCJGyG0Qes8[/youtube]
September 16, 2014
The Ultimate Weaponized Spyware For Computers and Smartphones: Now Free
As a Professor, attorney, and technologist, I deliver many academic lectures at John Jay College of Criminal Justice, lecture at conferences to professional organizations, and train law enforcement around the country. In 2012, I began warning of FinFisher, a German-based company (previously U.K.-based) that produces and sells computer intrusion systems, including remote monitoring solutions, and had recently developed the ultimate spyware for smartphones and computers.
Back then, details of FinFisher and its software were not publicly available. The company is secretive as its clients are government intelligence agencies. Some of FinFisher’s clients include nations with poor records on human rights, personal liberties, and privacy, including Mongolia, Pakistan, Vietnam, Nigeria, and Singapore. FinFisher has also reportedly sold software to intelligence communities in South Africa, Australia, Belgium, Slovakia, and the Netherlands.
In 2012, there was little information publicly available as to the full capabilities and reach of FinFisher’s software products. However, since then, information has slowly leaked out through WikiLeaks and other reputable sources. Today, FinFisher is known to produce the most powerful commercial weaponized surveillance malware software packages on the planet.
Two products of significance are FinSpy PC (computer spyware) and FinFisher Relay (smartphone spyware), which when installed grant the ability to intercept all files/documents and communications, such as those over Skype, email, and even video and audio through the webcam and microphone. These two software products can be remotely “pushed” (installed without the user’s knowledge or actions via a Trojan Horse or other method) to any computer or smartphone. This includes OS X, Windows and Linux computers, as well as Android, iOS, BlackBerry, Symbian, and Windows mobile devices. Users of these devices do not have to be anywhere near the vicinity of the person installing the malware. Furthermore, it is nearly impossible to identify that the malware has been installed without conducting a deep forensic analysis.
Disturbingly, researchers at citizenlab.org published evidence and reports showing the use of FinSpy PC and FinFisher Relay against journalists, activists, and political non-desirables around the world by government intelligence agencies. But at least the software was only available to international government intelligence agencies and generally kept out of the hands of cyber criminals… until now.
In 2013, during a presentation to the United States Association of Inspectors’ General, I warned that it was only a matter of time until FinFisher’s software would leak out on the web, becoming accessible to cyber criminals and others with malicious intent.
That day has arrived.
Yesterday, on September 15, 2014, Julian Assange, WikiLeaks Editor-in-Chief, allowed both FinSpy PC and FinFisher Relay to be openly published on WikiLeaks.org. In other words, as of yesterday, millions of cyber criminals around the world have access to a weaponized surveillance malware package that can be installed with very little effort, giving access to almost all the data on a user’s computer or smartphone.
Within minutes of the site going live, I received a barrage of communications via phone, email, Twitter, and text message from students, law enforcement, and researchers around the world. Most people just wanted to talk about the release of the software, while others asked how long it would take me to download and analyze the software.
Before lunchtime, my lab at John Jay College of Criminal Justice (The Advanced Research Domain for Information Security in Public Policy) had downloaded all available software and documentation. While my team and I obviously cannot deploy the software “in the wild,” we are able to analyze its code to determine exactly how virulent the software really is. We will be devoting a significant amount to time in the near future to analyze this threat and report our findings.
There is a glimpse of bright light shining through the murky water… Julian Assange and WikiLeaks did not release this software for cyber criminals to obtain and use, although it will be an unintended result. Their primary goal was to allow security researchers to analyze the code to come up with methods to protect us all (the public). While we are all at risk today, you can be sure that future software updates from Apple, Google, and Microsoft will contain significant security improvements rendering this software obsolete. That is, of course, until FinFisher updates the code within their products, and the cycle starts over again…
Adam Scott Wandt, J.D., M.P.A., is an Assistant Professor of Public Policy at John Jay College of Criminal Justice, where he serves on both the Graduate faculty of the Digital Forensics and Cyber Security program and the Masters of Public Administration in Inspection and Oversight program. Professor Wandt is an Attorney and Counselor-at-Law in the State of New York.
Media requests on this issue should be sent to the attention of [email protected] with FinFisher clearly identified in the subject line.
Professor Wandt On Twitter: @Prof_Wandt
August 27, 2014
Smartphone Security: Best Practices
When it comes to smartphone security, there are several “best practices” you can take to protect your data. First, be sure to always update your smartphone to the latest version of the operating system. This will ensure your smartphone receives important security updates that will help keep your data safe. Second, always use a password, even if you think you do not need one. Using a password tells the smartphone you want to keep the information safe, and most smartphones will actually handle your information/data differently than if you do not set up a password. Third, Android users should install anti-virus software. While iPhone users do not need to install anti-virus software, it is an absolutely necessity for Android users. Android users can download one of several free anti-virus programs from the Google Play store. Android users should also enable phone encryption, if supported by the phone model, which can be accessed in the “settings” menu. Android users should also make sure “USB Debugging” is disabled in the settings menu.
Finally, there is a five-step process you should engage in when you are ready to dispose of your smartphone. You should use this process no matter your method of disposal, whether you are disposing of your smartphone through a recycling program, gifting it to a friend, or selling it to someone through gazelle or e-bay, etc. Following this process will minimize the risk that others will be able to recover information/data after you wipe it.
(1) Reset your smartphone to factory default.
- Instructions for resetting iPhone: Access settings —> general —> reset —> erase all content and settings.
- Instructions for resetting Android: Varies by phone and provider. Look for “reset phone” or “reset phone to factory default” under the settings menu.
(2) Set the smartphone up again in order to access the App store (iPhone) or Google Play store (Android).
(3) Download and run a secure file shredder that will forensically wipe information from the device. I recommend the file shredder contained in a free secure communications application called Wickr. You can download Wickr from the App store (iPhone) or Google Play store (Android). Once installed, access “Secure Shredder” from the settings menu in Wickr and click “start.”
(4) Reset the phone again following the directions in step 1.
(5) Remove and keep SIM and MicroSD Cards.
While no method can absolutely guarantee your information/data is wiped completely from the phone, this proven method is a proven best practice to ensure that you keep yourself, family, friends, and co-workers safe.
WATCH THE WNBC 4 NEWS INVESTIGATIVE PIECE ON SMARTPHONE SECURITY
April 21, 2014
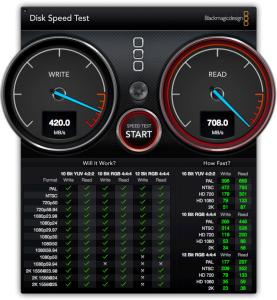
Disk Speed Test: Promise Pegasus R4 vs R6
After running disk speed tests on both the Promise Pegasus R4 and R6, we now pit them against each other in a Blackmagic speed test. Who will win?
[youtube]https://www.youtube.com/watch?v=-EGSN4cX32g[/youtube]
April 14, 2014
Disk Speed Test: Promise Pegasus R4 (RAID 5)
In this video I run a disk speed test on the Promise Pegasus R4 (RAID 5) Thunderbolt backup system using Blackmagic software.
[youtube]https://www.youtube.com/watch?v=BhQ8lIADKCU[/youtube]
April 7, 2014
Disk Speed Test: Apple Flash Storage
I ran a speed test on the Apple 751 Gb Flash Storage iMac 27-Inch Late 2012, 3.4 ghz, Intel i7 processor, 32 Gb RAM, using Blackmagic speed test software.
[youtube]https://www.youtube.com/watch?v=TwQh7hhz1tQ[/youtube]
March 31, 2014
Disk Speed Test: Promise Pegasus R6 (RAID 5)
I ran a speed test on the Promise Pegasus R6 (RAID 5) backup system. Watch the YouTube video below to see how the Pegasus stacks up.
[youtube]https://www.youtube.com/watch?v=qFqsKRNC6fo[/youtube]
March 24, 2014
Asus Google Nexus 7: YouTube Unboxing
In this unboxing we will take a look at the new Google Nexus 7 by Asus. This is the second generation Nexus 7 which was released with version 4.3 of Android Operation System. The Nexus 7 is an almost 8 inch tablet and is pretty light weight for it’s size at about 12 oz; it also comes with a 1280×800 pixel resolution screen. The Nexus has been praised for it’s price, processing, and hardware build. The tablet was criticized for a lack of rear-facing camera, and lack of expandable storage. This video goes through the unboxing of the tablet, I will release a review video soon.
[youtube]https://www.youtube.com/watch?v=DyjnwN-yspE[/youtube]
February 24, 2014
From Pizza to Apples
I first began teaching as an Adjunct in January 2005. I teach graduate school students who often work part- or full-time, have families and other responsibilities, and arrive to a 6 PM evening class tired after a full day of work or other activities. From the beginning, my standard policy was to treat my students to pizza or donuts once or twice a semester. I did this because I knew my students enjoyed it and appreciated it. Also, students seemed more attentive and likely to participate on the days I brought snacks.
Students always thankfully gobbled up every last bite. Most students were excited if there was enough for them to have two or even three slices of pizza, or two or three donuts. Over time, this changed. After a few semesters, I started to have leftovers. Students were taking less (only one slice of pizza or one donut), and some students would not take anything at all. Then, in fall 2013, I brought two dozen Dunkin’ Donuts to class one day. No one ate anything. Not one.
I asked the class why I had a full box of donuts left. Was is that it was too late for donuts? Would they prefer Krispy Kreme? Would they prefer ice cream? To my shock, the unanimous response was quite simple… they wanted healthy treats, like fruit. This was a radical shift from when I first started teaching nearly a decade ago.
Could it really be that over the past decade students were eating healthier and making healthier choices? I was skeptical, so I decided to do an experiment. Later that semester I brought to the same class one box of a dozen Dunkin’ Donuts and one bowl of assorted fruit (bananas, pears, oranges, and an assortment of different types of apples). To my surprise, the students did make the healthier choice. Some students even took more than one piece of fruit. I still remember seeing three apple cores on the desk of one student. In the end, not a single donut was eaten; Every piece of fruit was gone.
The only request the students had for future “fruitings” were some paper towels or napkins. I had two requests myself. First, students must clean up after themselves and not leave behind a mess. Second, I asked for volunteers to pick up the fruit on days my schedule made it difficult to do it myself.
Starting this semester, spring 2014, I implemented a new policy which is made easy by the fact that I only teach one traditional in-class course this semester with about 18 students. Every class I bring two bowls of fruit – a colander with apples and pears (I wash them before class), and a bowl of bananas and oranges. At almost every class session so far, every piece of fruit has been eaten.
I am quite amazed at the response less than $20 worth of fruit has on a graduate class that meets once a week from 6-8 PM. The students enjoy the evening pick-me-up so much that when I am very busy, they even volunteer to pick up the fruit, a position we have nicknamed the “fruit fetcher.” At the beginning of class students proudly declare, “I am the fruit fetcher and this week I have fetched your fruit.” (Okay, maybe that was paraphrased).
Bringing fruit to class may seem like a simple gesture, but really it is one way of letting my students know that I truly care about their preferences, well-being, and success. If for less than $20 a week some fruit will help my students have a more productive class session and thus help them succeed, then I am more than happy to help.
November 15, 2013
Mobile Device Investigations: Thinking Outside the Box
Professor Wandt’s Presentation at the Association of Inspectors’ General 2013 Annual Meeting. The topic of the presentation is “Mobile Device Investigations: Thinking Outside the Box.”
[youtube]http://www.youtube.com/watch?v=1LdZWTiWSBI[/youtube]
October 22, 2013
How to Perform a Clean Install of OS X 10.9 Mavericks by Creating an OSX 10.9 USB Installer

Creating a OS X 10.9 Mavericks USB Installer
With Apple’s announcement and release of OS X 10.9 Mavericks, many of you will want to perform a clean install by formatting your existing hard drive and starting from scratch. This brand new installation of the operating system will give you the look and feel of a new computer. Since Apple and the App Store do not natively support this, you will have to create a USB installer to do so. However, the method of creating a USB installer is slightly different than with previous versions of OS X. An additional benefit of creating a USB installer is that you won’t have to download the installer multiple times, if you own multiple Macs.
As with previous versions of OSX, you will need an 8 GB flash drive and the ability to download the installer (OS) from the App Store. I have created a simple step-by-step video on YouTube to help you through the process.
[youtube]http://www.youtube.com/watch?v=kbUetWXP4Xs[/youtube]
July 11, 2013
Problems with Equinox Gym?
I have had some major issues with the Equinox gym at columbus circle regarding billing and cancelation of membership. I feel their boilerplate policies are highly unjust and abusive. I am looking for people who may have suffered financial injury as a result of what I feel are unfair billing or cancelation practices. My goal is to obtain class action status in New York Supreme. Please contact me if you think you qualify. I will post updates here as things progress.
May 10, 2013
HTC ONE: 24 HOURS LATER
[youtube]http://www.youtube.com/watch?v=xx1f8Jm_22c[/youtube]
I have been using the AT&T HTC ONE for 24 hours now…. here is what you need to know.
How to Create a MAC OS X 10.8 Mountain Lion Install USB Flash Drive
[youtube]http://www.youtube.com/watch?v=Q7YvZxApGmg[/youtube]
It is more than just a little annoying that Apple won’t sell OS X 10.8 Mountain Lion on physical media. Only allowing download via the App store has its limitations for power users or IT shops. The solution is simple… create a MAC OS X 10.8 Mountain Lion Install USB Flash Drive. You can then use the USB drive to install / reinstall OS X as often as you want.